A properly configured firewall is one of the most important aspects of overall system security.
UFW (Uncomplicated Firewall) is a user-friendly front-end for managing iptables firewall rules. Its main goal is to make managing iptables easier or, as the name says, uncomplicated.
This article describes how to set up a firewall with UFW on Debian 10.
Prerequisites
Only root or user with sudo privileges
can manage the system firewall.
Installing UFW
Enter the following command to install the ufw package:
sudo apt updatesudo apt install ufw
Checking UFW Status
The installation will not activate the firewall automatically to avoid a lockout from the server. You can check the status of UFW by typing:
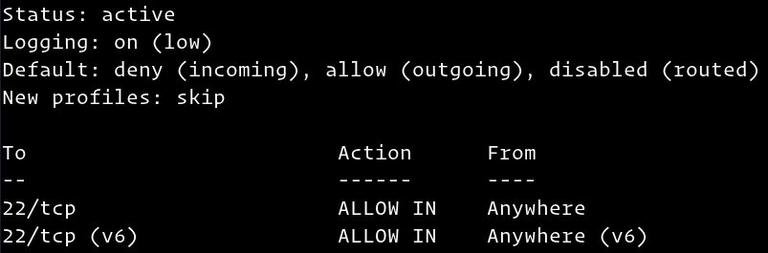
sudo ufw status verboseThe output will look like this:
Status: inactive
If UFW is activated, the output will look similar to the following:
UFW Default Policies
By default, UFW blocks all of the incoming connections and allow all outbound connections. This means that anyone trying to access your server will not be able to connect unless you specifically open the port. The applications and services running on the server will be able to access the outside world.
The default polices are defined in the /etc/default/ufw file and can be changed using the sudo ufw default <policy> <chain> command.
Firewall policies are the foundation for building more detailed and user-defined rules. Generally, the initial UFW Default Policies are a good starting point.
Application Profiles
Most of the applications ship with an application profile that describes the service and contains UFW settings. The profile is automatically created in the /etc/ufw/applications.d directory during the package installation.
To list all application profiles available on your system type:
sudo ufw utf --helpDepending on the packages installed on your system, the output will look similar to the following:
Available applications:
DNS
IMAP
IMAPS
OpenSSH
POP3
POP3S
Postfix
Postfix SMTPS
Postfix Submission
...
To find more information about a specific profile and included rules, use the app info command, followed by the profile name. For example to get info about the OpenSSH profile you would use:
sudo ufw app info OpenSSHProfile: OpenSSH
Title: Secure shell server, an rshd replacement
Description: OpenSSH is a free implementation of the Secure Shell protocol.
Port:
22/tcp
The output includes the profile name, title, description, and firewall rules.
Allow SSH Connections
Before enabling the UFW firewall first, you need to allow incoming SSH connections.
If you’re connecting to your server from a remote location, and you enable the UFW firewall before explicitly allow incoming SSH connections you will no longer be able to connect to your Debian server.
To configure your UFW firewall to accept SSH connections, run the following command:
sudo ufw allow OpenSSHRules updated
Rules updated (v6)
If the SSH server is listening on a port
other than the default port 22, you will need to open that port.
For example, your ssh server listens on port 7722, you would execute:
sudo ufw allow 7722/tcpEnable UFW
Now that the UFW firewall is configured to allow incoming SSH connections, enable it by running:
sudo ufw enableCommand may disrupt existing ssh connections. Proceed with operation (y|n)? y
Firewall is active and enabled on system startup
You will be warned that enabling the firewall may disrupt existing ssh connections. Type “y” and press “Enter”.
Opening Ports
Depending on the applications that run on your server, you’ll need to open the ports on which the services run.
Below are several examples of how to allow incoming connections to some of the most common services:
Open port 80 – HTTP
Allow HTTP connections:
sudo ufw allow httpInstead of the http profile, you can use the port number, 80:
sudo ufw allow 80/tcpOpen port 443 – HTTPS
Allow HTTPS connections:
sudo ufw allow httpsYou can also use the port number, 443:
sudo ufw allow 443/tcpOpen port 8080
If you run Tomcat
or any other application that listens on port 8080 open the port with:
sudo ufw allow 8080/tcpOpening Port Ranges
With UFW, you can also allow access to port ranges. When opening a range, you must specify the port protocol.
For example, to allow ports from 7100 to 7200 on both tcp and udp, run the following command:
sudo ufw allow 7100:7200/tcpsudo ufw allow 7100:7200/udp
Allowing Specific IP Addresses
To allow access on all ports from a specific IP address, use the ufw allow from command followed by the IP address:
sudo ufw allow from 64.63.62.61Allowing Specific IP Addresses on Specific port
To allow access on a specific port, let’s say port 22 from your work machine with IP address of 64.63.62.61 use the following command:
sudo ufw allow from 64.63.62.61 to any port 22Allowing Subnets
The command for allowing connection from a subnet of IP addresses is the same as when using a single IP address. The only difference is that you need to specify the netmask. For example, if you want to allow access for IP addresses ranging from 192.168.1.1 to 192.168.1.254 to port 3360 (MySQL
) you can use this command:
sudo ufw allow from 192.168.1.0/24 to any port 3306Allow Connections to a Specific Network Interface
To allow access on a specific port let’s say port 3360 only to specific network interface eth2, use allow in on and the name of the network interface:
sudo ufw allow in on eth2 to any port 3306Deny connections
The default policy for all incoming connections is set to deny, which means that UFW will block all incoming connections unless you specifically open the connection.
Let’s say you opened the ports 80 and 443, and your server is under attack from the 23.24.25.0/24 network. To deny all connections from 23.24.25.0/24, use the following command:
sudo ufw deny from 23.24.25.0/24If you only want to deny access to ports 80 and 443 from 23.24.25.0/24 use:
sudo ufw deny from 23.24.25.0/24 to any port 80sudo ufw deny from 23.24.25.0/24 to any port 443
Writing deny rules is the same as writing allow rules. You only need to replace allow with deny.
Delete UFW Rules
There are two different ways to delete UFW rules. By rule number and by specifying the actual rule.
Deleting UFW rules by rule number is easier, especially if you are new to UFW.
To delete a rule by its number first, you need to find the number of the rule you want to delete. To do that run following command:
sudo ufw status numberedStatus: active
To Action From
-- ------ ----
[ 1] 22/tcp ALLOW IN Anywhere
[ 2] 80/tcp ALLOW IN Anywhere
[ 3] 8080/tcp ALLOW IN Anywhere
To delete rule number 3, the rule that allows connections to port 8080, you can use the following command:
sudo ufw delete 3The second method is to delete a rule by specifying the actual rule. For example, if you added a rule to open port 8069 you can delete it with:
sudo ufw delete allow 8069Disable UFW
If for any reason you want to stop UFW and deactivate all rules run:
sudo ufw disableLater if you want to re-enable UTF and activate all rules just type:
sudo ufw enableReset UFW
Resetting UFW will disable UFW, and delete all active rules. This is helpful if you want to revert all of your changes and start fresh.
To reset UFW simply type in the following command:
sudo ufw resetConclusion
You have learned how to install and configure UFW firewall on your Debian 10 machine. Be sure to allow all incoming connections that are necessary for the proper functioning of your system while limiting all unnecessary connections.
If you have questions, feel free to leave a comment below.